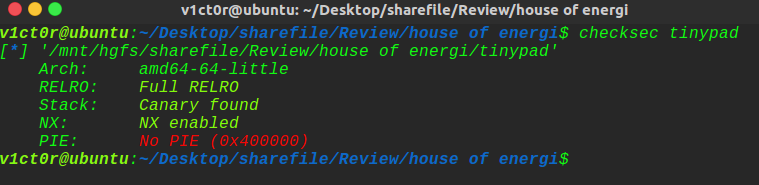
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
| int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3;
int v4;
signed int size;
__int64 v6;
unsigned __int64 v7;
int c;
int i;
int idx;
int v12;
int size_1;
unsigned __int64 v14;
v14 = __readfsqword(0x28u);
v12 = 0;
write_n(&unk_4019F0, 1LL);
write_n(
" ============================================================================\n"
"// _|_|_|_|_| _|_|_| _| _| _| _| _|_|_| _|_| _|_|_| \\\\\n"
"|| _| _| _|_| _| _| _| _| _| _| _| _| _| ||\n"
"|| _| _| _| _| _| _| _|_|_| _|_|_|_| _| _| ||\n"
"|| _| _| _| _|_| _| _| _| _| _| _| ||\n"
"\\\\ _| _|_|_| _| _| _| _| _| _| _|_|_| //\n"
" ============================================================================\n",
563LL);
write_n(&unk_4019F0, 1LL);
do
{
for ( i = 0; i <= 3; ++i )
{
LOBYTE(c) = i + 49;
writeln("+------------------------------------------------------------------------------+\n", 81LL);
write_n(" # INDEX: ", 12LL);
writeln(&c, 1LL);
write_n(" # CONTENT: ", 12LL);
if ( *&chunk[16 * (i + 16LL) + 8] )
{
v3 = strlen(*&chunk[16 * (i + 0x10LL) + 8]);
writeln(*&chunk[16 * (i + 0x10LL) + 8], v3);
}
writeln(&unk_4019F0, 1LL);
}
idx = 0;
v4 = getcmd();
v12 = v4;
if ( v4 == 'D' )
{
write_n("(INDEX)>>> ", 11LL);
idx = read_int("(INDEX)>>> ", 11LL);
if ( idx > 0 && idx <= 4 )
{
if ( *&chunk[16 * (idx - 1 + 16LL)] )
{
free(*&chunk[0x10 * (idx - 1 + 16LL) + 8]);
*&chunk[16 * (idx - 1 + 16LL)] = 0LL;
writeln("\nDeleted.", 9LL);
}
else
{
writeln("Not used", 8LL);
}
}
else
{
writeln("Invalid index", 13LL);
}
}
else if ( v4 > 'D' )
{
if ( v4 != 'E' )
{
if ( v4 == 'Q' )
continue;
LABEL_43:
writeln("No such a command", 17LL);
continue;
}
write_n("(INDEX)>>> ", 11LL);
idx = read_int("(INDEX)>>> ", 11LL);
if ( idx > 0 && idx <= 4 )
{
if ( *&chunk[16 * (idx - 1 + 16LL)] )
{
c = 48;
strcpy(chunk, *&chunk[16 * (idx - 1 + 16LL) + 8]);
while ( toupper(c) != 'Y' )
{
write_n("CONTENT: ", 9LL);
v6 = strlen(chunk);
writeln(chunk, v6);
write_n("(CONTENT)>>> ", 13LL);
v7 = strlen(*&chunk[16 * (idx - 1 + 16LL) + 8]);
read_until(chunk, v7, 0xAu);
writeln("Is it OK?", 9LL);
write_n("(Y/n)>>> ", 9LL);
read_until(&c, 1uLL, 0xAu);
}
strcpy(*&chunk[16 * (idx - 1 + 16LL) + 8], chunk);
writeln("\nEdited.", 8LL);
}
else
{
writeln("Not used", 8LL);
}
}
else
{
writeln("Invalid index", 13LL);
}
}
else
{
if ( v4 != 'A' )
goto LABEL_43;
while ( idx <= 3 && *&chunk[16 * (idx + 16LL)] )
++idx;
if ( idx == 4 )
{
writeln("No space is left.", 17LL);
}
else
{
size_1 = -1;
write_n("(SIZE)>>> ", 10LL);
size_1 = read_int("(SIZE)>>> ", 10LL);
if ( size_1 <= 0 )
{
size = 1;
}
else
{
size = size_1;
if ( size_1 > 0x100 )
size = 0x100;
}
size_1 = size;
*&chunk[16 * (idx + 16LL)] = size;
*&chunk[16 * (idx + 16LL) + 8] = malloc(size_1);
if ( !*&chunk[16 * (idx + 16LL) + 8] )
{
writerrln("[!] No memory is available.", 27LL);
exit(-1);
}
write_n("(CONTENT)>>> ", 13LL);
read_until(*&chunk[16 * (idx + 16LL) + 8], size_1, 0xAu);
writeln("\nAdded.", 7LL);
}
}
}
while ( v12 != 'Q' );
return 0;
}
|